August 2015 virus activity review from Doctor Web
OREANDA-NEWS. August 2015 witnessed the appearance of a new Trojan designed to infect routers running Linux and a new dangerous miner that has a set of features typical of worms and can spread across a network by itself. Moreover, in August, security researchers detected a downloader Trojan distributed in Microsoft Word documents, an installer of unwanted applications belonging to the LoadMoney family, and a number of new malicious programs targeting Android.
Threat of the month
With the appearance of electronic currency, virus makers were given an opportunity to find a new way of stealing money from users—for that, miner Trojans were created. However, as the amount of resources that needed to be spent on creation of such applications constantly grew, cybercriminals started loosing their interest in this sphere. Nevertheless, in August, Doctor Web analysts had another chance to examine a Trojan belonging to the mentioned category. The malicious program was named Trojan.BtcMine.737.
On the inside, Trojan.BtcMine.737 looks like a Russian doll—it consists of three installers nested in each other. The first “layer” contains a simple dropper that, once launched, tries to kill all processes of Trojan.BtcMine.737 if they are running. It also extracts an executable file of another installer from its body, plants it into a temporary folder, runs it, and deletes the original file. The second installer has a wider set of features that are typical of network worms. When activated, this installer saves the executable file to some folder on the infected computer and runs it. Then it replicates itself to several folders making one of them accessible from the local network. The installer's copies look like WinRAR archives with the Key name.
After that, the malicious program copies itself to root folders of all hard drives and goes through all computers in network places trying to connect to them by using logins and passwords from a special list. Moreover, if necessary equipment is available, Trojan.BtcMine.737 sets up an open Wi-Fi access point. If a connection to any computer on the network is established, the Trojan tries to replicate itself to that computer and run the copy. The CNminer.exe program, saved to a hard drive by Trojan.BtcMine.737 during the second step of the installation, is, in fact, the installer of a mining utility. Find out more about the malware in this news article.
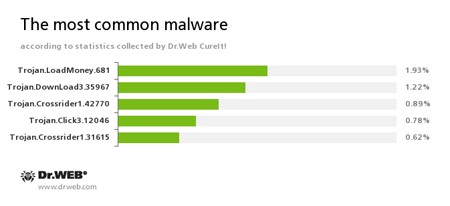
According to the statistics gathered by Dr.Web CureIt!
-
Trojan.LoadMoney
A family of downloader programs generated by servers belonging to the LoadMoney affiliate program. These applications download and install unwanted software on the victim's computer.
-
Trojan.DownLoad3.35967
A Trojan that can download other malicious programs from the Internet and install them on the infected computer.
-
Trojan.Crossrider
A family of malicious programs designed to display various advertisements to Internet users.
-
Trojan.Click
A family of malicious programs designed to generate traffic for various websites by redirecting users to the corresponding webpages.
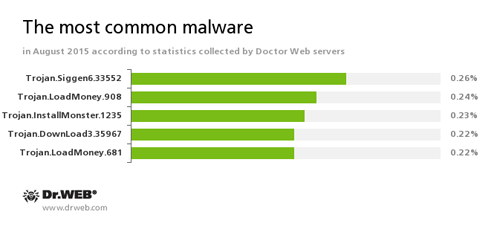
According to Doctor Web statistics servers
-
Trojan.LoadMoney
A family of downloader programs generated by servers belonging to the LoadMoney affiliate program. These applications download and install unwanted software on the victim's computer.
-
Trojan.Installmonster
A family of malicious programs created using the Installmonster affiliate program. These programs install various unwanted software on the victim's computer.
-
Trojan.DownLoad3.35967
A Trojan that can download other malicious programs from the Internet and install them on the infected computer.
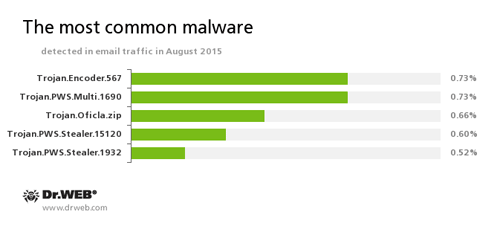
-
Trojan.Encoder.567
A malicious program belonging to the family of encryption ransomware Trojans that encrypt files and demand a ransom for decryption of compromised data. This program can encrypt important user files, for example, of the following types: .jpg, .jpeg, .doc, .docx, .xls, xlsx, .dbf, .1cd, .psd, .dwg, .xml, .zip, .rar, .db3, .pdf, .rtf, .7z, .kwm, .arj, .xlsm, .key, .cer, .accdb, .odt, .ppt, .mdb, .dt, .gsf, .ppsx, .pptx.
-
Trojan.PWS.Multi.1690
A banking Trojan designed to steal confidential information stored on the infected computer.
-
Trojan.Oficla
A family of Trojans mainly distributed via email messages. Once one of these Trojans infects a system, it hides its further activity. Trojan.Oficla connects the computer to a botnet, which allows cybercriminals to upload other malicious software to the compromised machine. After the system gets infected, cybercriminals that run the botnet get control over the victim’s computer. In particular, they become able to upload, install, and use any malicious software they choose.
-
Trojan.PWS.Stealer
A family of Trojans designed to steal passwords and other confidential information stored on the infected computer.
Botnets
In August, Doctor Web security researchers continued to monitor two subnets belonging to the botnet created by cybercriminals using the Win32.Rmnet.12 file infector. Their average activity is shown in the following graphs:
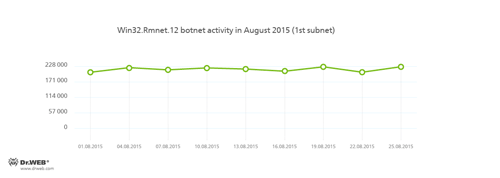
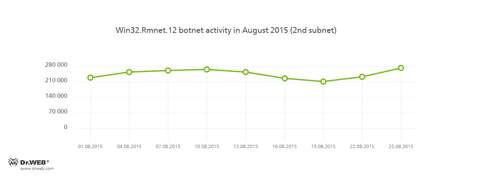
Rmnet is a family of viruses spread without any user intervention. They can embed content into loaded webpages (this theoretically allows cybercriminals to get access to the victim's bank account information), steal cookies and passwords stored by popular FTP clients, and execute other commands issued by cybercriminals.
The botnet consisting of computers infected with Win32.Sector is still active. Its average daily activity can be seen in the following picture:
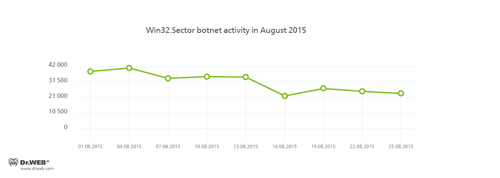
Win32.Sector can perform the following actions:
- Download various executable files via P2P networks and run them on infected machines.
- Inject its code into running processes.
- Prevent some anti-viruses from operating and block access to the websites of their respective developers.
- Infect files on local disks, removable media (where the malware creates the autorun.inf file during the infection process), and in shared folders.
In August, cybercriminals controlling the Linux.BackDoor.Gates.5 botnet became more active and intensified their attacks on various Internet resources—in comparison with the previous month, the number of attacked IP addresses increased by 118.3 per cent and was estimated 2,083. As before, most targets of the attacks were located in China (86.7 per cent), while 10.7 per cent of compromised websites were hosted in the United States.
Encryption ransomware
The number of requests for decryption received by Doctor Web technical support service
| July 2015 | August 2015 | Dynamics |
|---|---|---|
| 1,414 | 1,425 | +0.77% |
The most common ransomware programs in August 2015
- Trojan.Encoder.567
- Trojan.Encoder.858
- BAT.Encoder
Dr.Web Security Space 10.0 for Windows
protects against encryption ransomware
This feature is not available in Dr.Web Anti-virus for Windows
| Preventive Protection | Data Loss Prevention |
|---|---|
 |
 |
More information
Linux
In August 2015, Doctor Web security researchers examined a number of malicious programs that can infect routers running Linux.
One of those Trojans, dubbed Linux.PNScan.1, was distributed in a rather peculiar way—Doctor Web analysts presume that initially Linux.PNScan.1 was installed on attacked routers by virus makers themselves. For that, they exploited the ShellShock vulnerability running a script with relevant settings. Subsequently, the malware got uploaded and installed on devices by Trojans belonging to the Linux.BackDoor.Tsunami family, which, in turn, are distributed using Linux.PNScan.1. This malicious program serves the only purpose—to brute-force router access passwords. If the hacking attempt is successful, the Trojan uploads a malicious script that downloads and installs backdoors based on the router architecture (ARM, MIPS, or PowerPC). The script can also download a relevant backdoor if by exploiting the Shellshock vulnerability cybercriminals succeed to hack an Intel computer (x86). The mentioned backdoors can execute various intruder-issued commands. For example, upon a command from cybercriminals, the applications can download Tool.Linux.BrutePma.1. This tool is used to hack administrative control panel of PHPMyAdmin which is used to manage relational databases.
Moreover, on servers controlled by cybercriminals, Doctor Web analysts detected other malicious programs among which is a modification of Linux.PNScan.2 and a Trojan named Trojan.Mbot whose main task is to hack websites. Another detected Trojan was dubbed Perl.Ircbot.13. It serves the purpose of looking for vulnerabilities in websites created on a number of CMS platforms and in websites that use certain online-store management systems. 1,439 devices are known to be infected with the mentioned malicious programs; at that, in 649 cases, geographical location of infected devices was also determined:
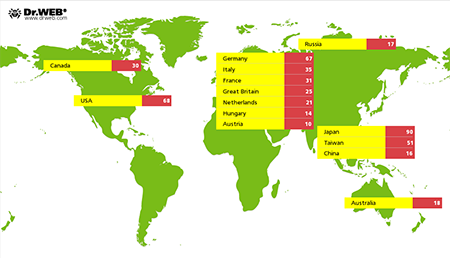
More information about the malicious programs detected by Doctor Web security researchers and details regarding the mentioned incident can be found in this news article.
Other malicious applications
In August 2015, Doctor Web security researchers examined a dangerous downloader Trojan named W97M.DownLoader.507 and distributed as a Word document attached to email messages. To be able to read the contents of such a document, the user is prompted to enable macros in Word.
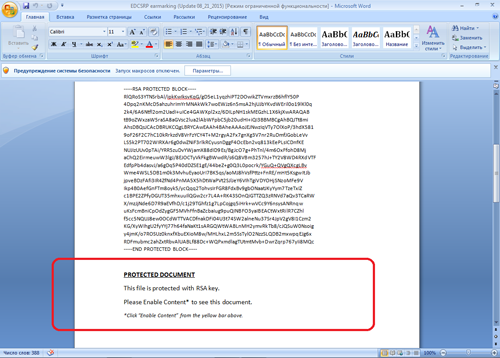
After macros are activated, the text is shown to the victim. At the same time, the Trojan starts downloading several code fragments from the remote server. Using these fragments, the malicious program generates several scripts which, in turn, download from the server controlled by cybercriminals a dangerous banking Trojan and then run it. Find out more about the Trojan in this news article.
Another malicious application examined in Doctor Web virus laboratory in August is called Trojan.LoadMoney.336. This installer of unwanted programs can be found on personal computers quite often. The Trojan's distribution scheme looks as follows: if the user attempts to download some file stored on a file-sharing resource controlled by cybercriminals, they are redirected to a website from which Trojan.LoadMoney.336 is downloaded to the computer. Once launched, the Trojan connects to a remote server and receives a configuration file. The file contains links to different affiliate applications (sometimes malicious ones) that the Trojan downloads and runs on the infected computer.
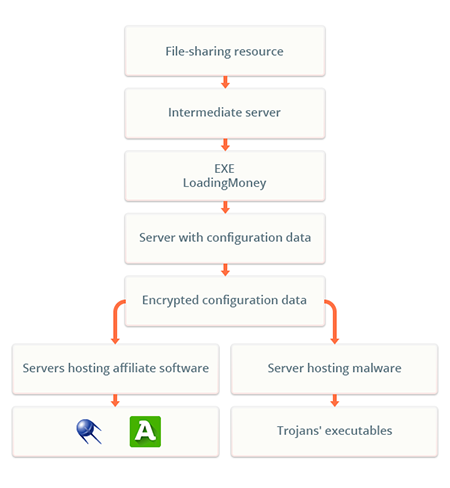
Dangerous websites
During August 2015, 834,753 URLs of non-recommended websites were added to Dr.Web database.
July 2015August 2015Dynamics| +821,409 | +834,753 | +1.62% |
Malicious and unwanted programs for Android
In comparison with the previous months, August proved to be rather calm in terms of mobile security events. However, Android devices continued to remain the main target of cybercriminals specializing in creation and distribution of mobile malware. For example, in August, Doctor Web security researchers detected a new Android Trojan designed for spying. Moreover, during the last summer month, new dangerous ransomware, banking Trojans, and SMS Trojans grew in number. Among the most noticeable events related to malware for Android we can mention
- New cases of Android Trojans being employed by cybercriminals to spy on users
- Banking Trojans continue to threaten mobile devices' owners
- Distribution of new Android ransomware
- Growing number of SMS Trojans
Find out more about malicious and unwanted programs for Android in our special overview.
Learn more with Dr.Web
Virus statistics Virus descriptions Virus monthly reviews Laboratory-live




Комментарии