May 2016 virus activity review from Doctor Web
OREANDA-NEWS. The last spring month was marked by the emergence of a new backdoor for Microsoft Windows that was mainly designed to monitor user activity and to steal files from the infected computer. In addition, malware for Android continues to infect mobile devices—thus, our analytics registered a number of mobile banking Trojans has considerably increased. Besides, Doctor Web specialists examined a Trojan that was able to transform an infected machine into a proxy server.
Threat of the month
Spyware Trojans pose a very serious threat because they can steal very important private information. BackDoor.Apper.1 is one of such-like Trojans, which was detected at the beginning of May.
The Trojan is distributed via a dropper in the form of the Microsoft Excel file with a special macros. This macros collects a self-extracting archive by bytes and runs it. The archive consists of an executable file, which has a valid digital signature registered to Symantec, and a dynamic library, in which all the main functions of the Trojan are implemented. Once launched, this file loads the malicious dynamic library into the memory of the infected computer.
BackDoor.Apper.1 is mainly designed to steal files from the machine. Yet, the backdoor can execute other commands.
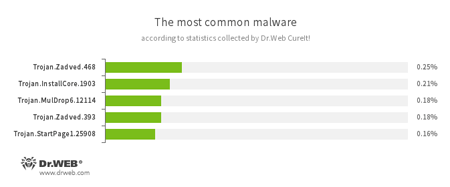
According to statistics collected by Dr.Web CureIt!
-
Trojan.Zadved
This Trojan displays fake search results in the browser window and imitates pop-up messages from social networking sites. In addition to this, the malware can replace advertisements displayed on different Internet resources. -
Trojan.InstallCore.1903
A Trojan that can install unwanted and malicious applications. -
Trojan.MulDrop
А Trojan that can install other malicious programs on the computer. -
Trojan.StartPage
A malware family that can modify the home page in the browser settings.
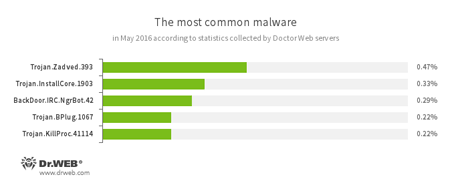
According to Doctor Web statistics servers
-
Trojan.Zadved
This Trojan displays fake search results in the browser window and imitates pop-up messages from social networking sites. In addition to this, the malware can replace advertisements displayed on different Internet resources. -
Trojan.InstallCore.1903
A Trojan that can install unwanted and malicious applications. -
BackDoor.IRC.NgrBot.42
A fairly common Trojan, which is known to information security researchers since 2011. Malicious programs of this family are able to execute intruder-issued commands on infected machine controlled by cybercriminals via the IRC (Internet Relay Chat) text-messaging protocol. -
Trojan.BPlug
These plug-ins for popular browsers display annoying advertisements to users as they browse webpages. -
Trojans designed to kill running processes of other applications and to perform other malicious functions on the infected device.
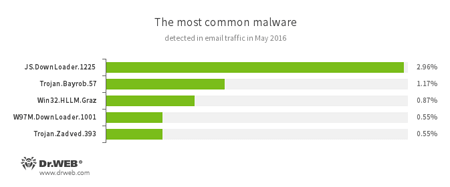
Statistics concerning malicious programs discovered in email traffic
-
JS.Downloader
A family of malicious scripts that are written in JavaScript and designed to download and install other malware programs on the computer. -
Trojan.Bayrob.57
A Trojan that can steal confidential information from the compromised computer and perform other malicious actions. -
Win32.HLLM.Graz
An worm that is distributed via mass mailing. It monitors traffic of the specified ports and parses transmitted data in order to retrieve passwords. This data is then used to spread the worm. -
W97M.DownLoader
A family of downloader Trojans that exploit vulnerabilities of office applications and can download other malicious programs to the compromised computer.
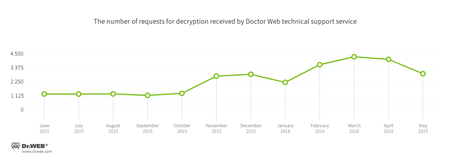
Encryption ransomware
The most common ransomware programs in May 2016
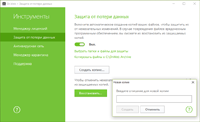
Dr.Web Security Space 11.0 for Windows
protects against encryption ransomware
This feature is not available in Dr.Web Anti-virus for Windows.
| Data Loss Prevention | |
|---|---|
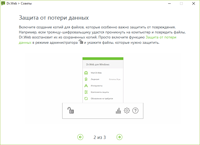 |
 |
Dangerous websites
During May 2016, Doctor Web added 550,258 URLs into the Dr.Web database of non-recommended sites.
| April 2016 | May 2016 | Dynamics |
|---|---|---|
| +749,173 | +550,258 | -26.55% |
Other threats
TeamViewer is a popular tool of remote control. Specialists and system administrators use it to access to the system via a network and, for example, change some settings or send necessary files. However, this utility can be used by cybercriminals as well—they has modified the program so that its icon is not displayed on the Windows notification area, which helps to connect to the computer without user knowledge.
BackDoor.TeamViewer.49 also implements functions of TeamViewer. Yet, in this case, TeamViewer plays another role: the Trojan uses this program to load the library responsible for performing main malicious functions to the memory. Therefore, the computer starts operating as a proxy server that redirects traffic from the C&C server to the specified remote server. To learn more about BackDoor.TeamViewer.49, refer to the review published by Doctor Web.
Malicious and unwanted programs for mobile devices
Banking Trojans for Android are still dangerous, which is proved by the fact that in May, these malicious programs were again used by virus makers to steal money from owners of mobile devices. At that, Android.SmsSpy.88.origin was still being distributed in order to attack users all over the world. Besides, Doctor Web specialists discovered a huge number of websites containing Android.BankBot.104.origin and other banking Trojans.
Among the most noticeable May events related to mobile malware, we can mention
- New version of Android.SmsSpy.88.origin that has already infected dozens of Android apps worldwide.
- Banking Trojans that were being spread via fraudulent websites offering users to download game cheating software.




Комментарии