May 2016 mobile malware review from Doctor Web
OREANDA-NEWS. In May, Doctor Web analytics registered a spike in banking Trojans’ activity. At that, virus makers continued to spread Android.SmsSpy.88.origin that has infected mobile devices of bank customers all over the world. Moreover, cybercriminals were actively using fraudulent websites to distribute Android.BankBot.104.origin together with other banking Trojans.
PRINCIPAL TRENDS IN MAY
Mobile threat of the month
Banking Trojans still pose a serious threat for Android users. One of such programs is Android.SmsSpy.88.origin that was first spotted in 2014. From that time, it became more sophisticated and has already compromised bank clients’ mobile devices worldwide. In the past month, virus makers continued to distribute Android.SmsSpy.88.origin.
Android.SmsSpy.88.origin has the following features:
- Steals login credentials for user accounts of online banking applications, displaying a bogus authentication dialog on top of the running banking service (the number of attacked programs amounts to 100)
- Steals credit card information, displaying a bogus dialog of the Google Play payment service settings
- Intercepts incoming SMS messages and stealthily sends text messages
- Locks the home screen upon cybercriminals’ command and demands a ransom to unlock it
- Hinders operation of anti-virus programs preventing them from launching
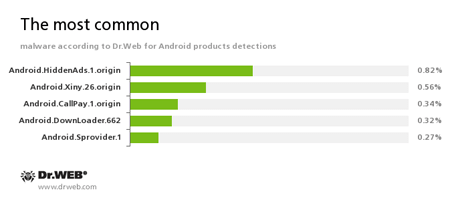
According to statistics collected by Dr.Web for Android
-
Android.HiddenAds.1.origin
A Trojan designed to display advertisements. It is distributed under the guise of popular apps by other malicious programs that are covertly installed into the system directory. -
Android.Xiny.26.origin
A Trojan that gets root privileges, installs itself into the system directory, and then is able to download various applications without user knowledge. In addition, it displays annoying advertisements. -
Android.CallPay.1.origin
A Trojan that provides access to adult content while covertly making phone calls to premium numbers as a payment for this service. -
Android.DownLoader.662
A Trojan designed to download and install other malware to the compromised computer. -
Android.Sprovider.1
A Trojan for Android designed to display advertisements in the status bar and to download and install other applications including malicious ones.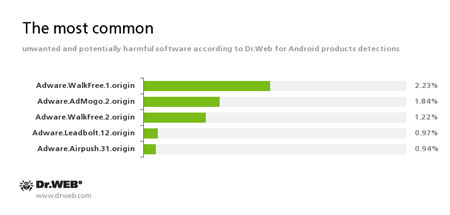
-
Adware.WalkFree.1.origin
-
Adware.AdMogo.2.origin
-
Adware.WalkFree.2.origin
-
Adware.Leadbolt.12.origin
-
Adware.Airpush.31.origin
An unwanted program module that is incorporated into the Android applications and is responsible for advertising on mobile devices.
Banking Trojans
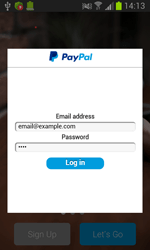
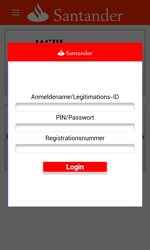
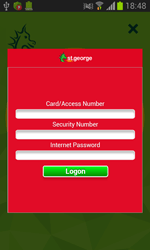
Apart from Android.SmsSpy.88.origin, other banking Trojans were also attacking Android devices. Doctor Web specialists discovered a big number of fraudulent websites distributing banking Trojans—in particular, Android.BankBot.104.origin. These resources offer users to download game cheating programs. Yet, if the victim tries to download such-like software, they are immediately redirected to another website that, in fact, distributes the Trojan.
Once the Trojan is on, it attempts to steal money from the user’s bank accounts, intercepts incoming text messages, and covertly sends SMS messages.
Banking Trojans for Android represent a serious danger for users because attackers very often use social engineering to trick victims into downloading these malicious programs. Thus, Doctor Web specialists strongly advise you against downloading software from unreliable resources.




Комментарии